Recently, I’ve been becoming more interested in protecting my privacy and security online, given the threat of a zombie apocalypse or general country-wide tyrannical overlord.
I don’t like the new security measures of having to text to log into so many useless applications. It was a major hassle for me when I was traveling as a digital nomad. I was just trying to get into my accounts!
I’ve also become more interested in the “prepper” movement (aka survivalism).
Society is a very useful tool, but it’s not always on your side. So, I wanted to put together a list of a few effective ways that I’ve found to safeguard your security to ensure that you always have the upper hand when you’re on the internet.
I hope you find the list to be helpful!
1. Protect Your Online Payments with Privacy.com
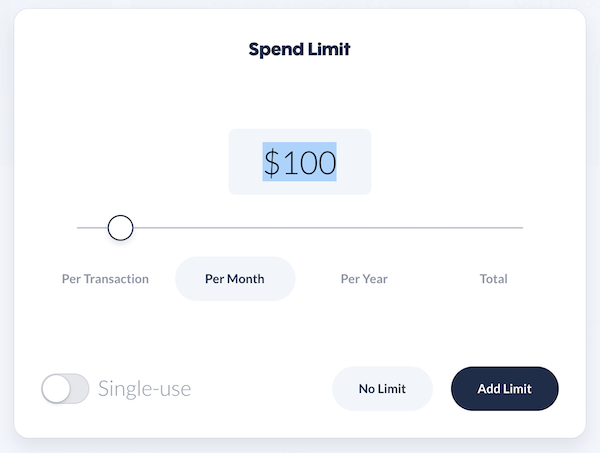
I LOVE this website (and app). You can have ALL of your online payments go through this website and set up disposable debit cards that YOU control.
This means that the next time a merchant is being difficult, rather than calling your credit card company or your bank, you can easily just turn off the card within Privacy.com. You can also create cards that have spend limits, either per month or per transaction.
You can make a single-use card, so that even if a merchant wants to charge you again with the same card, they can’t!
This puts the power in your hands as a consumer. Also, for those “free 30 day trial” offers, you can make sure that they can’t even charge your card if they tried after those 30 days.
What’s also awesome is you can use a FAKE NAME or address if you want to. It doesn’t matter when you check out with the merchant.
2. Google Voice
This has been around for a while, but I want to highlight why Google voice is such a powerful tool. First of all, there is a lot of personal information tied to your actual phone number. People can figure out where you live and what your name is.
Google Voice will give you a new phone number that you can use to make or receive phone calls. That way, it’s much harder to track you. In addition, you can use the text message feature so that you can get texts at your email inbox.
This is great for two-factor identification. This way, you can give the website a bogus number, and if you’re out of the country, you can still access that number easily. Keep in mind, some applications can detect when you’re using a Google voice number, but others can’t.
3. Coinbase
Coinbase is an easy way that you can buy and sell virtual currency like Bitcoin and Eretheum.
Why would you want virtual currency? Because inherently, the value of the US dollar is tied to the government. The government can decide to print money or not. Also, the currency fluctuates relative to other currencies around the world.
In the same way that you might buy gold or another commodity as a way to diversify your assets, you can use virtual currency, with one added bonus.
It’s psuedo-anonymous when you make transactions. This means that it’s a bit harder to detect when you’re using a virtual currency to make purchases (or accept payments) as when you’re using traditional cash. This helps to protect your privacy.
If you want to get REALLY hardcore, then you could look into some of the much more anonymous virtual currencies here.
In addition, if you already have some virtual currency, you may want to look into more effective ways of storing those assets using something like a different type of wallet.
For example, Ledger Nano X is The Best Crypto Hardware Wallet. It’s extremely secure as composed to an online interface, like Coinbase.
- Ledger Nano has a higher degree of security standards. It also makes it so your coins aren’t vulnerable to a cyber attack.
- You can also easily trade on the go using your smartphone’s bluetooth connection.
- You can manage many different types of crypto easily.
What’s the point of holding assets if they are easy to identify through research and scrutiny? This makes it a bit easier to safeguard your privacy.
4. Nord VPN
This is almost a no-brainer, but if you’ve never heard of a VPN, it’s basically an effective way to MASK where you’re accessing the internet from.
Your IP is easily trackable. Hackers and others can quickly see where you are accessing the internet from (along with your internet service provider). If you don’t like the idea of other people snooping on you, then I’d recommend looking into getting a VPN.
This VPN is great because you can easily change the location of the server from which you’re accessing the internet. You can switch from NYC to Tokyo to Europe with just a few clicks. This does a few things:
- Allows you to access content that is restricted or not restricted in certain countries
- Fool your internet service provider, so they don’t know which website you’re visiting
- Browse the internet with relatively complete anonymity
- Bypass marketing tactics (like purchasing cheaper online tickets because of the region you’re searching from).
There are a lot of VPNs out there, but at the time of writing, Nord is the gold standard.
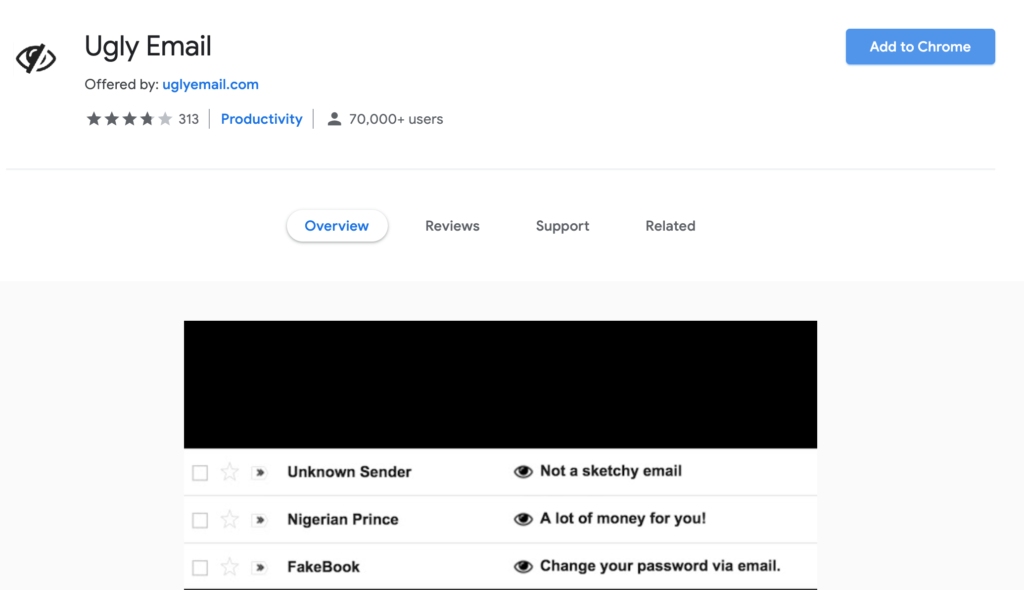
5. Ugly email
Ugly Email is a simple application that you can use to see who is tracking your emails. Marketers and PR managers do this all the time! Rather than being tracked, you can use an app like this to make sure that your information stays secure.
“When a tracker is detected, it shows the icon of an eyeball in the subject line to alert you that a tracker is hidden inside the email. Rest assured that all detected trackers are blocked and you can freely open your emails.”
These are just a few tools that I recommend you consider to get started. There are way more out there, like Tor browser, and we haven’t even talked about file storage.
There are affiliate links in this article.